Do you truly value your online privacy? Yes, and in today’s digital landscape, a reliable virtual private network (VPN) is no longer a luxury, but a necessity. The purpose of this guide is to help you navigate the complex world of VPN, which exposes the major features and providers that prefer your oblivion above all others.
We understand your anxiety about protecting personal data from prying, whether they are from cyber criminals, advertisers, or even from your own ISP. So we have done careful research and compiled a list of the best VPN for privacy 2025, ensuring that you can take an informed decision for an unbeatable shield against online monitoring.
Get ready to recover your digital freedom.
The Ever-Growing Need for Online Privacy in 2025
In an era where every click, search, and online interactions are carefully tracked, the concept of digital privacy seems increasingly delicate. Governments are expanding monitoring capabilities, masking individual data, and cyber criminals are constantly looking for weaknesses. Without adequate protection, your online activities can portray a detailed picture of your life, susceptible to exploitation.
This is the place where a strong VPN becomes unavoidable. It acts as a digital cloaking device, encrypts your internet traffic, and masks your IP address, making monitoring your online appearance make unreliablely difficult for anyone. As we proceed to 2025, the demand for privacy-centered VPN is at an all-time high, inspired by a global awakening to data exploitation and a desire for true digital autonomy.
What Makes a VPN Truly Privacy-Focused?
Not all VPNs are made the same, especially when privacy is your paramount concern. While many advertise strong encryption, true privacy is far ahead of that. Here are those important factors that we have considered when identifying the best VPN for privacy 2025:
1. No-Logs Policy: The Cornerstone of Privacy
A real no-logs policy means that the VPN provider does not store any data that can identify you or your online activities. It also includes:
- Uses log: No records of websites were seen, files downloaded, or used services.
- Connection log: No timestamps, incoming/outgoing IP address, connection duration, or VPN server.
To be reliable for a no-logs policy, it must be:
- Audited independently: The third-party audit by reputed firms verifies the claims of the Audit VPN, which provides a fair assessment of their logging practices.
- Transparent: VPN should clarify whether, if any, minimal data that they collect (eg, for billing or troubleshooting, but anytime identifying use data).
- Ram-Kaval Server: This advanced technology ensures that no data is ever written on a hard drive. When the server is rebooted, all data is erased, privacy is greatly enhanced.
2. Jurisdiction: Location Matters
The country in which a VPN company is legally based determines laws and data retention policies that have to be followed. Ideally, a privacy-centered VPN should be located in a jurisdiction outside the reach of Five Eyes, Nine Eyes, or Fourteen Eyes, such as intelligence-sharing alliances. These alliances include countries that agree to collect and share intelligence information, potentially compromising user data, even if a VPN has a strict no-log policy.
3. Robust Encryption Standards
Encryption is the backbone of VPN security. The best VPN for privacy 2025 appoints industry-municipality encryption to scrape its data, making it until it becomes unlimited parties.
- AES-256 (Advanced encryption standard with 256-bit key): This is the standard of gold for encryption, which is considered almost unbreakable by modern computing power.
- Perfect Forward Secretary (PFS): It ensures that a new, unique encryption key is generated for each session, which means that if a key is compromised, the past and future communications are safe.
4. Advanced Security Features
Beyond the basic encryption, some features significantly increase your privacy and anonymity:
- Kill Switch (Network Lock): This crucial feature automatically disconnects your Internet if the VPN connection drops unexpectedly. This prevents your actual IP addresses and activities from being exposed for a short moment. There are usually two types:
- System-Level Kill Switch: Blocks all internet traffic on your device if VPN is disconnected.
- Application-Level Kill Switch: If the VPN connection is dripping, it allows you to specify what applications should be blocked if offered more granular control.
- DNS Leak Protection: DNS (Domain Name System) Requests Translate Website Names to IP Addresses. DNS leaks occur when these requests are sent outside the encrypted VPN tunnel, which reveals your browsing activity to your ISP. Privacy-centered VPN routes all DNS requests through its own secure DNS servers, preventing such leaks.
- IPV6 leak security: Similar to DNS leaks, IPV6 leaks can highlight your actual IP address if your system defaults for IPV6 connections outside the VPN tunnel. Top VPNs provide strong IPV6 leakage protection.
- Obfuscation (Stealth VPN): This technique disrupts your VPN traffic as regular internet traffic, making it difficult for ISPs or governments to find out that you are using VPN. This is particularly useful in countries with heavy internet sensorship.
- Multi-hop (double VPN): Routes its traffic through two different VPN servers in different places, adds an additional layer of encryption, and makes even more difficult to detect its online activity.
5. Anonymous Payment Options
For ultimate privacy, some VPNs offer payment methods like cryptocurrency or even cash, allowing you to subscribe without linking your identity to the service.
Top 5 Best VPN for Privacy in 2025
After extensive research and rigorous testing, here are our top picks for the Best VPN for privacy 2025:
| VPN Provider | Key Privacy Features | Jurisdiction | Audit Status | Price Range (approx. monthly) |
| NordVPN | Strict No-Logs (audited, RAM-only servers), Double VPN, Onion over VPN, Threat Protection | Panama | Multiple | $3.00 – $5.00 |
| Proton VPN | Strict No-Logs (audited, open-source apps), Secure Core, Stealth, Tor over VPN | Switzerland | Multiple | $5.00 – $8.00 |
| ExpressVPN | Strict No-Logs (audited, TrustedServer technology), Lightway Protocol, Kill Switch | BVI | Multiple | $6.00 – $9.00 |
| Mullvad VPN | No-Logs (audited), Anonymous accounts (no email), Cash payments, WireGuard | Sweden | Multiple | Flat $5.00 (approx. €5) |
| Surfshark | Strict No-Logs (audited, RAM-only servers), MultiHop, Camouflage Mode, Unlimited devices | Netherlands | Multiple | $2.00 – $4.00 |
Best VPN for privacy 2025: 1. NordVPN
Overview: NordVPN ranks as a top contender for constant overall VPN service, and its commitment to privacy is particularly strong. Located in Panama, there is no data retention law with a confidential jurisdiction. NordVPN conducts a strict no-logs policy that has been audited independently several times. Their entire server network runs on the RAM-only server (trustedster technology), ensuring that no data is ever permanently stored.
- Major privacy features:
- Strict No-Legs Policy: Verified by PWC and Deloitte independent Audit, confirming that they do not monitor, store, or log user activity.
- Panama Jurisdiction: Working outside the impact of any compulsory data retention laws and intelligence alliance from any country.
- Ram-Kaval Server: All servers run on volatile memory, which means that all data is erased on reboot, increasing privacy and security.
- Double VPN (Multi-Hop): Rolls its traffic through two different VPN servers, adding an additional layer of encryption and obfuscation.
- Onion on VPN: With the safety of VPN, it combines the oblivion of TOR.
- Danger protection: VPN blocks advertisements, trackers, and malicious websites at the level.
- Automatic Kill Switch: If the VPN connection falls, the data is prevented leaks.
- DNS and IPV6 leak protection: Ensure that your actual IP and DNS queries are never exposed.
Why this is unbeatable for privacy: NordVPN’s comprehensive approach to privacy, supported by advanced Audit, Ram-Caval Server, and Double VPN like advanced features, makes an extraordinarily strong option for users who prefer oblivion.
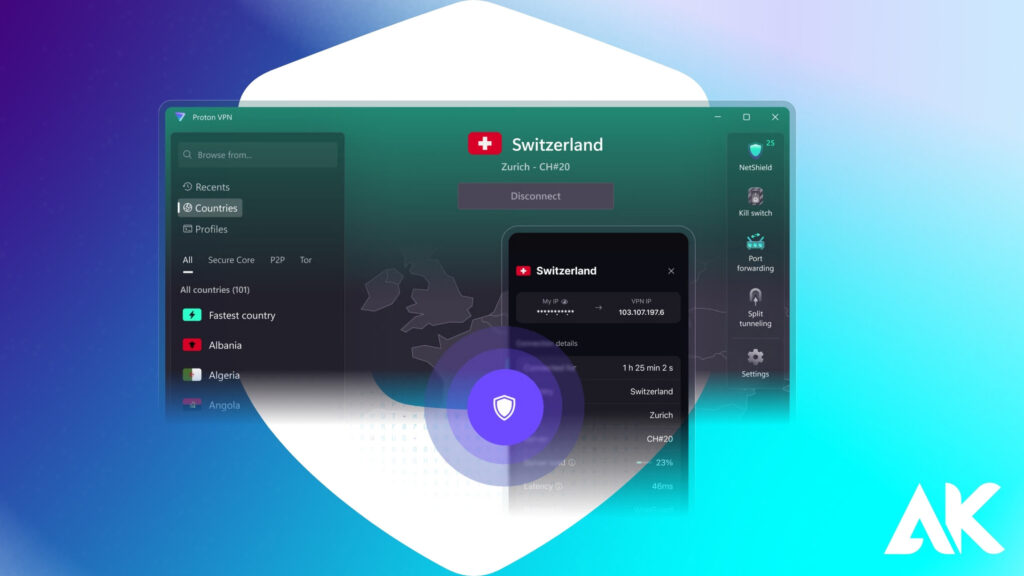
Best VPN for privacy 2025: 2. Proton VPN
Overview: Developed by the creators of ProtonMail, a highly secure email service, Proton VPN is built from the ground up with privacy and security as its main mission. Located in Switzerland, a country famous for its strong privacy laws, Proton VPN provides transparent operations and open-source applications.
- Major privacy features:
- Strict No-Legs Policy: Audit independently, and is a main principle of their service. They collect exactly no identifiable user data.
- Swiss jurisdiction: Switzerland claims some of the world’s strongest privacy laws and is not part of any intelligence-sharing alliance.
- Safe core server: Before joining network attacks, to protect from network attacks, user traffic is routed through the rigid server located in privacy-friendly countries (eg, Switzerland, Iceland, Sweden).
- Open-Sure Apps: All proton VPN applications are open-source and undergo independent security audit, allowing anyone to observe their code for weaknesses.
- Chupke protocol: Their obfuscation technology helps bypass strong firewalls and VPN blocks.
- Tor Over VPN: Dedicated servers that automatically route your traffic through the Tor Network.
- Always on VPN and Kill Switch: It ensures that your connection is always preserved, and if the VPN drops, it immediately blocks the Internet access.
- DNS leak security: Prevents your DNS requests from being exposed.
- Unnamed Payment: Bitcoin supports payment for increased oblivion.
Why this is unbeatable to privacy: Proton VPN’s privacy, transparent practices, unwavering commitment to Swiss jurisdiction, and innovative features such as safe core and open-source apps make it a top-level choice for privacy advocates.
3. ExpressVPN
Overview: ExpressVPN is a widely respected VPN provider known for its speed, credibility and strong security currency. Located in the British Virgin Islands (BVI), no data with retention laws, expresswpn works under a verified no-logs policy. Their proprietary lightway protocol is designed for speed and safety without compromising confidentiality.
- Major privacy features: Best VPN for privacy 2025
- Audited No-Legs Policy: Their no-logs policy is independently audited by Cure53, which confirms their claims.
- British Virgin Islands (BVI) jurisdiction: a secrecy suited to compulsory data retention and intelligence alliance.
- Trustedserver Technology (Ram-Only Servers): All server data is erased regularly, as servers walk on RAM, not hard drive, no permanent log.
- Lightway protocol: A custom-made, open-source VPN protocol that is light, fast, and extremely safe.
- Network Lock (Kill Switch): A strong kill switch automatically blocks all internet traffic. If VPN drops connections, your IP address protection.
- DNS and IPV6 leak protection: Underlying safety measures to prevent any casual data exposure.
- Split Tunneling: It allows you to choose which apps use VPN and which directly reach the Internet.
Why this is unbeatable for privacy: ExpressVN’s commitment to independent audit, its privacy-friendly jurisdiction, and its innovative trustecerswar technology makes it a highly reliable option to maintain online oblivion.
4. Mullvad VPN
Overview: Mulvad VPN is a unique provider that greatly emphasizes user oblivion and privacy. Located in Sweden, Mulwad works with a minimum approach to data collection, even anonymous account construction and cash payment. They are known for their transparency and direct pricing.
- Major privacy features:
- Zero-Leakage Policy: Mulvad clearly states that they do not log down to any activity, connection, bandwidth, or IP address. Their no-log claims are independently audited.
- Unnamed Account Building: You do not require an email address or any personal information to create an account. You have just been assigned a random account number.
- Cash payments have been accepted. For final oblivion, you can mail their office to pay for your membership.
- Open-Sure Apps: Their desktops and mobile applications are open-sourced and pass through regular audits.
- Wireguard support: The modern and efficient Wireguard takes advantage of the protocol for fast and safe connections.
- Building Kil Switch: If the VPN connection is interrupted, no data is leaked.
- DNS and IPV6 leak protection: comprehensive security against different types of leaks.
- Multi-hop: provides an option to root traffic through two servers for increased privacy.
Why this is unbeatable to privacy: Mulvad stands for its unmatched commitment to oblivion, from VPN account construction to payment methods. If your priority is complete privacy and reducing any link to your identity, Mulvad is an extraordinary option.
5. Surfshark
Overview: Surfshark has gained rapid popularity for its impressive feature set, strong safety, and unlimited simultaneous connections. Located in the Netherlands (which is part of the nine Eis Alliance), Surfshark reduces it by maintaining a strict, audit no-logs policy and operating a full network of RAM-only servers.
- Major privacy features:
- Audited No-Togs Policy: Although in a Five Eyes country, Surfshark’s policy has been independent and verified, Giving Users Confidence.
- Ram-Kaval Server: All servers are discourse, which means that no user data can be permanently stored or recovered.
- Cleanweb: DNS blocks advertisements, trackers, and malware at the level, increases privacy and browsing speed.
- Camoufuscation: To reveal your VPN traffic as regular internet traffic, it is useful in a restrictive environment.
- Multihop (double VPN): Rolls its connection through two VPN servers for additional safety and oblivion.
- Bypassseer (split tunneling): allows you to select the applications or websites to bypass VPN connections.
- Automatic Kill Switch: Protects your data in case of unexpected VPN disconnects.
- DNS and IPV6 leak protection: comprehensive leakage prevention measures.
- Unlimited simultaneous connection: Protect all your equipment and even share your account with family, ensuring comprehensive privacy.
Why it is unbeatable for privacy: Despite its jurisdiction, Surfshark’s strict, no-logs policy, Ram-keval server, and strong suit of secrecy-growing features, combined with unlimited connections, make it an excellent and inexpensive option for privacy-conscious users in 2025.
Key Factors to Consider When Choosing Your VPN
Beyond our top picks, while choosing the Best VPN for privacy 2025, here is a checklist of important ideas:
- Cost vs. Price: While free VPN may look attractive, they often compromise privacy by logging data or displaying infiltration advertisements. Investing in a prestigious payment VPN is important for real privacy. Look for providers that offer good value for money, especially on longer-term plans.
- Server Network and Speed: A comprehensive server network usually means low congestion and better speed. While privacy is paramount, a VPN that slows down your connection can cause disappointment. See for providers with a good balance of privacy and performance.
- Ease of use: User-friendly applications are important in various platforms (Windows, macOS, Android, iOS, Linux). A VPN should also be easy to set up and use for non-technical users.
- Customer Assistance: Responsible and knowledgeable customer aid (preferably 24/7 live chat) is important to prevent any issue. (Best VPN for privacy 2025)
- Money-Back Guarantee: Most reputable VPNs provide a 30-day money-back guarantee, allowing you to conduct service-free tests before committing.
How to Maximize Your Best VPN for Privacy 2025
Using VPN is an important step towards better online privacy, but it is not only one. To maximize your oblivion and safety really.
- Always continue your VPN: Make sure your VPN is active until you are online, especially on the public Wi-Fi network.
- Enable Kill Switch: Always activate your VPN’s Kill Switch feature to prevent contingency data leaks.
- Verify the DNS/IPV6 leaks: Use the online tool to check DNS or IPV6 leaks on time -time to ensure that your VPN is working correctly.
- Use safe browsers: Pair your VPN with privacy-centered browsers such as Brave or Firefox (with extended tracking protection) and consider advertisements and extensions that block trackers.
- Practice good digital hygiene: Use strong, unique passwords, enable two-factor authentication, and beware of fishing efforts.
- Regular update software: Keep your operating system, browser, and VPN client software updated to benefit from the latest security patch.
- Be aware of your digital footprint: even with a VPN, be cautious about the personal information you share online.
The Future of Online Privacy and VPNs in 2025
As technology evolves, so do the challenges to online privacy. For Best VPN for privacy 2025, in 2025, we can expect:
- Expression of surveillance: Governments and corporations will continue to develop more advanced methods of data collection and monitoring.
- The rise of quantum computing: Although still the latest, the development of quantum computers poses a long-term threat to current encryption standards. VPN providers will need to adapt to quantum-resistant encryption.
- Great demand for transparency: Users will demand more transparency from VPN providers related to their L-Ging Ging Methods and Security ITS Ditts.
- Integration with other privacy tools: VPN will probably be part of a comprehensive suite of browser privacy tools, more integrated with secure browsers, encrypted messaging applications, and decentralized technologies.
Choosing the best VPN for privacy 2025 is an investment in your digital freedom and security. Understanding the important characteristics that really define privacy-centered service and selecting a provider that aligns with your needs, you can navigate the Internet with confidence and peace of mind, knowing that your online activities are your own.
FAQs
Question: Why is a “no-logs” policy so crucial for the Best VPN for privacy 2025?
Answer: A no-logs policy is the bedrock of a privacy-focused VPN because it guarantees the provider doesn’t record any data about your online activities, like websites visited or files downloaded. Without these logs, there’s no data to hand over to authorities or third parties, even if requested, making it impossible to trace your digital footprint back to you.
Question: How do I know if a VPN truly delivers the Best VPN for privacy 2025 experience?
Answer: To verify a VPN’s privacy claims, look for independent third-party audits of their no-logs policy and security infrastructure. Also, prioritize VPNs that use RAM-only servers, which automatically wipe data with every reboot, and are based in privacy-friendly jurisdictions outside of intelligence-sharing alliances.
Question: Can using the Best VPN for privacy 2025 guarantee complete online anonymity?
Answer: While a top-tier VPN significantly enhances your privacy by encrypting your traffic and masking your IP, absolute online anonymity is extremely difficult to achieve. A VPN is a powerful tool, but it should be combined with other good digital hygiene practices like using secure browsers, strong passwords, and being mindful of the personal information you share online to maximize your privacy.